Running Kurtosis in Kurtosis Cloud
Kurtosis Cloud is a fully managed cloud offering and accompanying self-service workflows for a stress-free, easy way to deploy test and dev environments, that live as long as you need them to, directly onto remote infrastructure. By logging into our cloud portal, a cloud instance will be provisioned to run your test and dev enclaves.
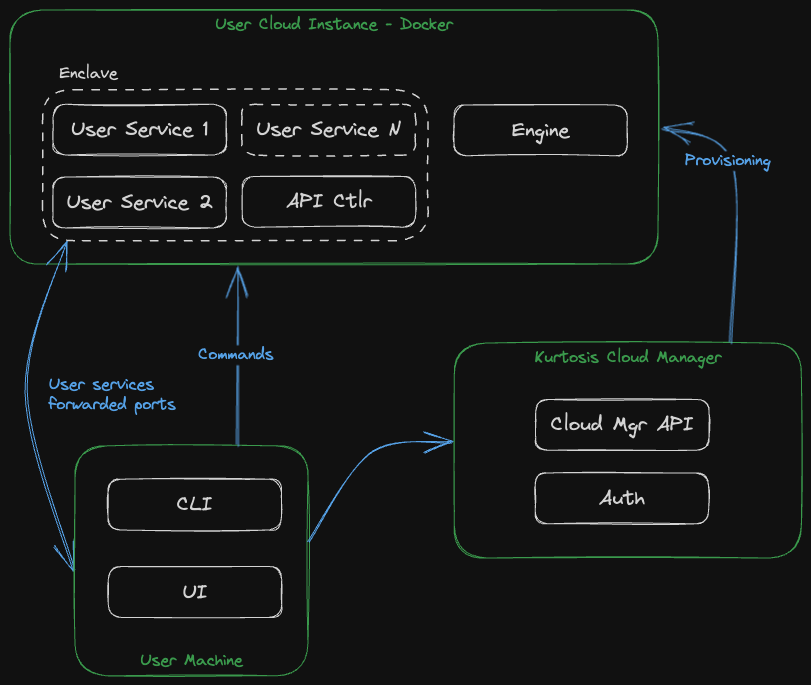
You can interact with your enclaves using the UI (or the CLI for more advanced use cases).
A Kurtosis cloud instance is an AWS EC2 instance running the Kurtosis engine, the Kurtosis API controller and your enclave services inside Docker. The service ports are forwarded to your local machine.
Advantages of running Kurtosis enclaves in Kurtosis Cloud
In addition to offloading the compute to a cloud infrastructure, Kurtosis Cloud comes with other advantages. When provisioning a cloud instance, Kurtosis will create a specific AWS user account and a storage space in S3.
Services running inside a Kurtosis enclave in Kurtosis Cloud can freely read and write objects from/to this S3 storage.
While only the owner of the S3 storage is permitted to write to the S3 storage, the data is publicly accessible to anyone that knows the object key. For this reason, we don't recommend storing sensitive data in the S3 storage.
The AWS user key as well as the information on the user S3 space is provided to all Starlark packages running in the
cloud via the global kurtosis module. The following variables are available inside Starlark and can be passed as
environment variables or simple arguments to the services started inside the enclave:
kurtosis.aws_access_key_idandkurtosis.aws_secret_access_key: The AWS user key pair required to authenticate to AWSkurtosis.aws_bucket_region,kurtosis.aws_bucket_nameandkurtosis.aws_bucket_user_folder: The bucket region and name, as well as the specific user folder the AWS user is authorized to access.
The AWS user created has a very restricted set of permissions by default. It can only read and write to its user folder inside the S3 bucket. But it is possible to request more access, reach out to us via Discord or by email.